If you would like to purchase paid user accounts for your team, contact sales@dragon1.com.
You can generate Cybersecurity Architecture Blueprints with this Dragon1 demo by doing the Demo Steps.
The example Cybersecurity Reference Architecture you see is an interactive example of a generated Blueprint in the Viewer. This application can be used on dragon1.com/viewer, but it can also be embedded on any website or run locally on your laptop or server.
We have provided an Excel Sheet you can use to generate Cybersecurity Architecture.
Dragon1 supports you in analyzing the generated Cybersecurity Architecture blueprint and managing your transformation within your company using the diagram and dashboard.
Generating Cybersecurity Reference Architecture in Viewer
Below is a static visualization of the Cybersecurity Reference Architecture. You can use the buttons on the button bar to switch on and off a category of items.
Cybersecurity Security Architecture Blueprints to Lower Risks
Cybersecurity is a complex issue that keeps many organizations busy.
One way to get a grip is to generate a security blueprint, a capability heatmap, and a roadmap.
Read more about creating a security blueprint for digital banking
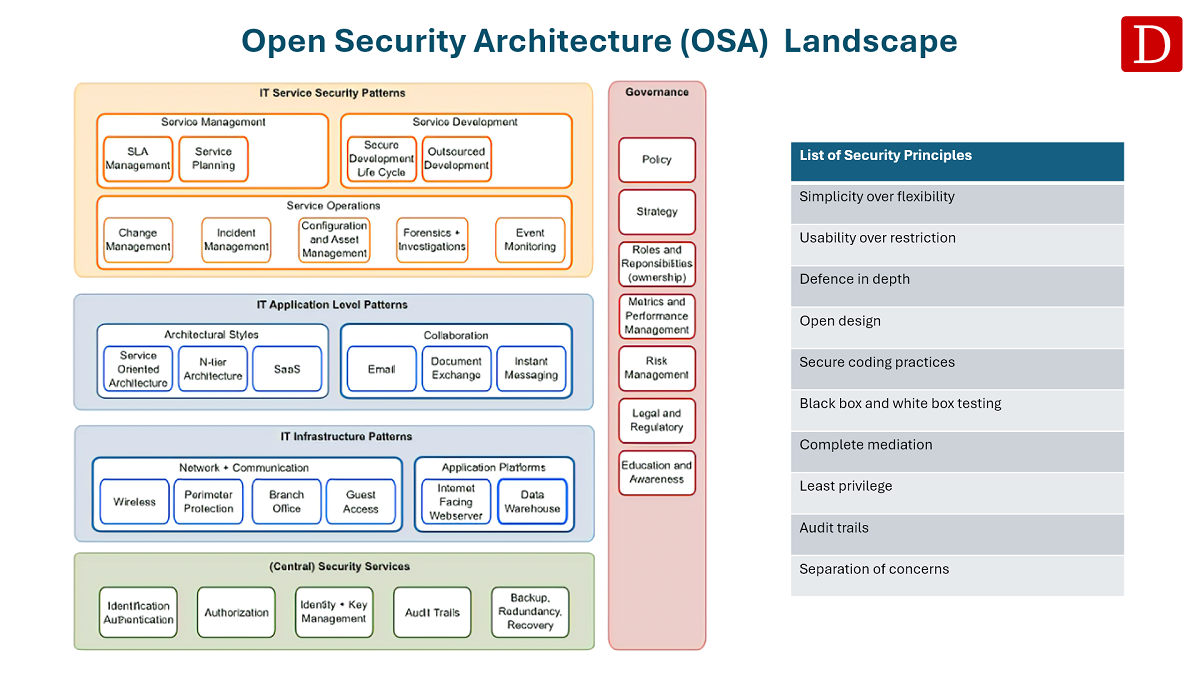
Open Security Architecture (OSA) Landscape
What is the Open Security Architecture (OSA)?
Open Security Architecture (OSA) is the name of a framework related to security controls, both functional and technical.
OSA as a framework provides professionals with an overview of essential concepts, principles, patterns, controls, components, and issues for security.
In many architecture decisions, these items are involved in designing better and more effective security architectures and solutions.
Dragon1 supports creating your own applied version of this framework and measuring and improving your compliance with this framework.
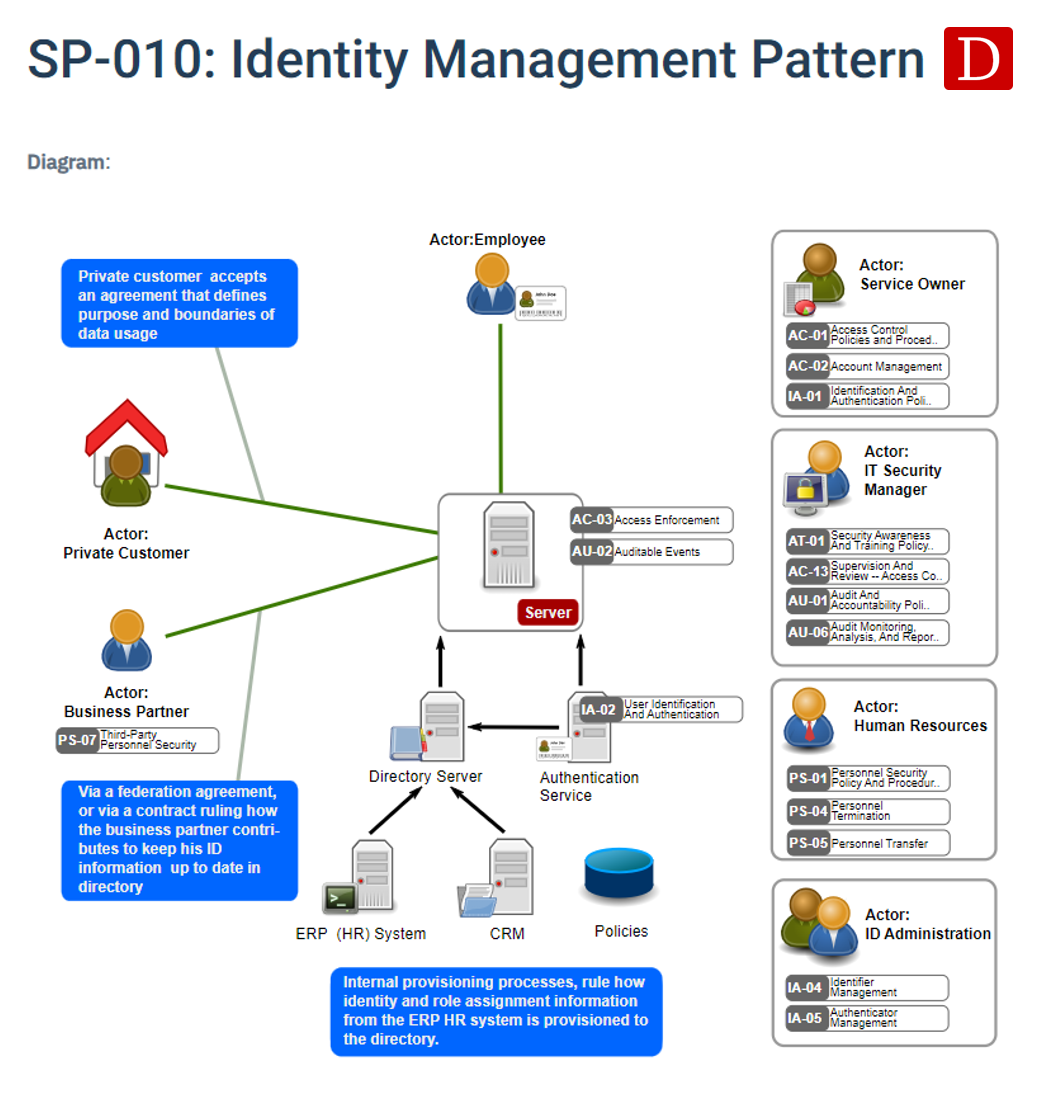
Identity Management Pattern
Dragon1 supports modeling your own version of the security patterns provided by OSA.
Here you see a 1-on-1 example of the Identity Management Pattern.
Dragon1 also supports modeling the OSA security controls with any architecture visualization or diagram.
Take Your First Step: Create a Free Trial Account
Upload your data in the Excel sheet directly to the Viewer or administer it in the Dragon1 repository. Get started with a trial account!
For seamless (re)use of your company data, upload it to your paid user account. Obtain your Dragon1 PRO license today from the Online Store.