Executive Briefing: CISO, Security Architects & SOC Analysts
90% Faster Threat Neutralization via AI UML State Machine Diagrams
AI-Driven Cybersecurity Threat Intelligence
How to automate the lifecycle of threat detection and mitigation?
The Dragon1 AI UML Software Architect Tool models the complex states of cyber threats, defining precise transitions from detection to automated containment and long-term intelligence archiving.
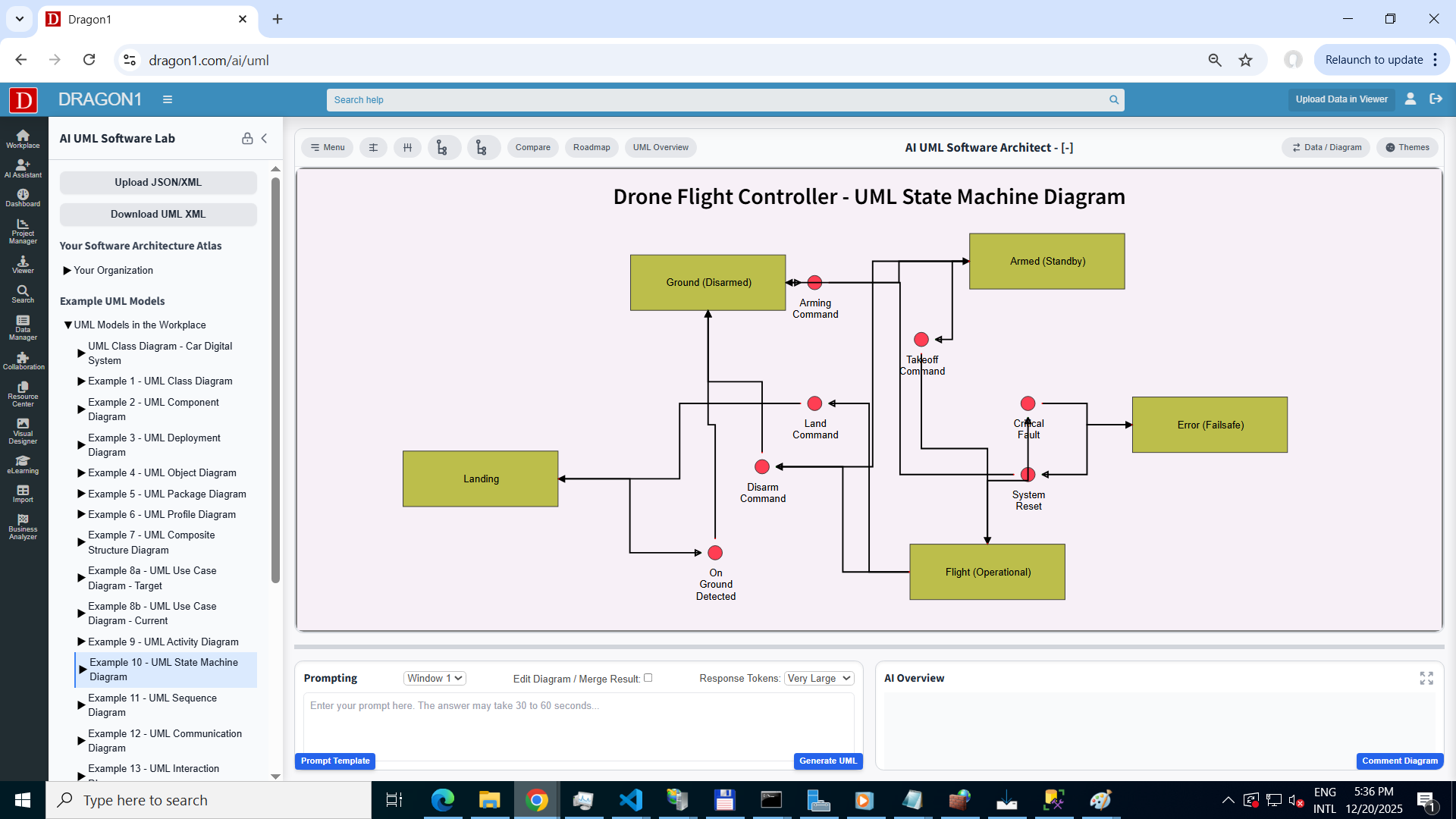
1. Current State (As-Is) - Static Security Logging
Manual Status Updates | Fragmented Threat Context
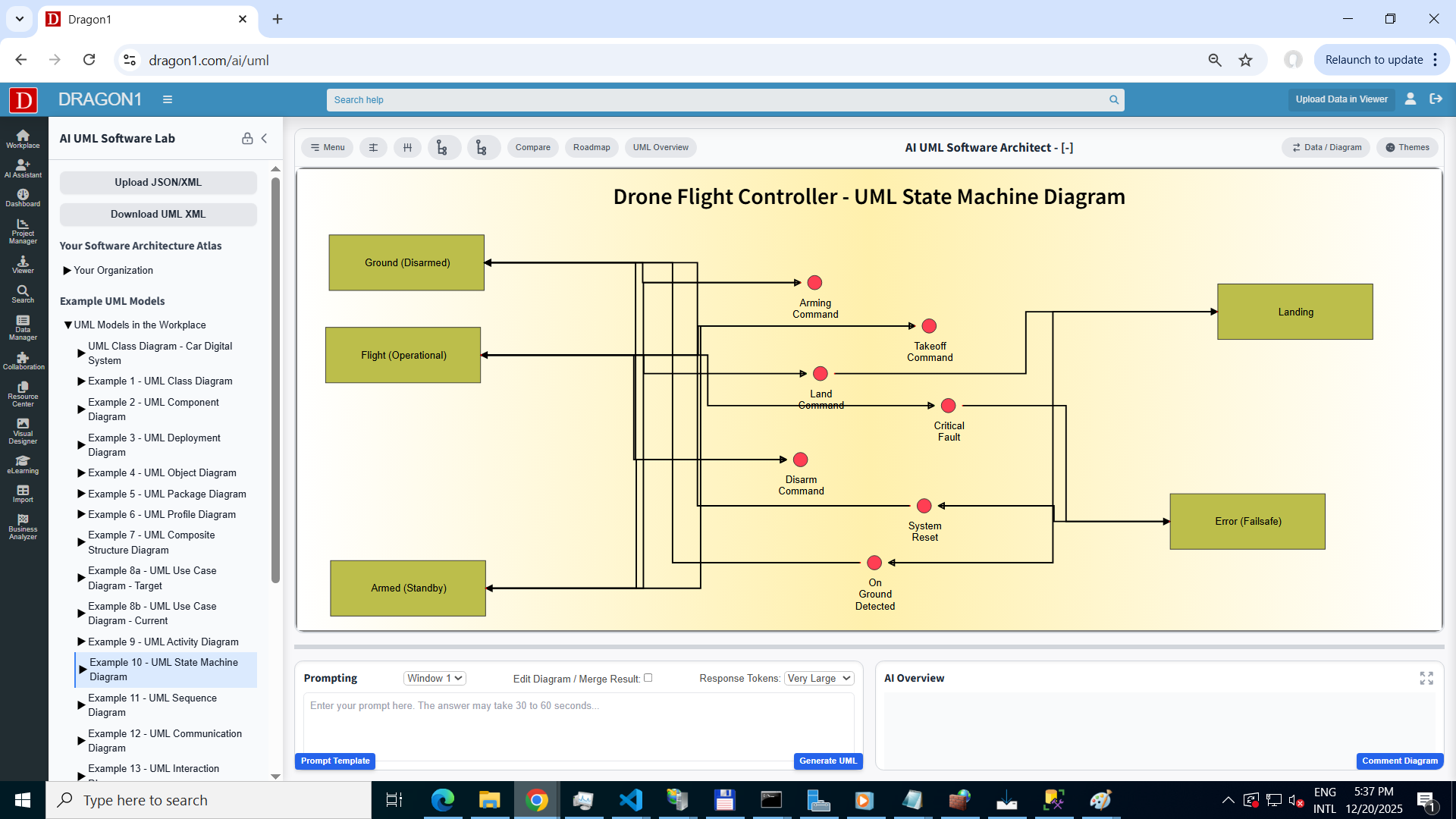
2. Target State (To-Be) - Automated State Transitions
Real-Time Adaptive Response | Deterministic Logic
AI-Powered Scenario Modeling & Time-Lapse Visualization
Security ROI & Impact
Stateful Security: Reducing the Window of Vulnerability
80%
Reduction in Mean Time to Contain (MTTC) by automating state transitions for known attack patterns.
99.9%
Consistency in incident handling by enforcing state-based compliance protocols.
Zero
Zombie alerts; every detected threat must progress through a defined state or be formally dismissed.
The Enterprise Result: Proactive Defense
Autonomous
Containment Logic.
AI agents transition threats to a 'Contained' state instantly upon detecting high-confidence indicators of compromise (IoC).
Dynamic
Risk Re-scoring.
Threat states are continuously updated as new intelligence is ingested, escalating or de-escalating priority automatically.
Traceable
Audit Readiness.
Every state change is timestamped and logged, providing a perfect record for regulatory compliance and forensics.
Threat Handling Comparison: State Efficiency
1. Current State (As-Is): Reactive Incident Response
Threats exist in loosely defined 'statuses' across different tools, leading to communication gaps and slow response times.
| Analysis | Manual status changes in a ticketing system. | Threat remains 'Active' longer than necessary due to administrative lag. |
2. Future State (To-Be): AI-Orchestrated State Machine
The AI UML Software Architect tool generates the system boundary, which enforces a strict state machine. Transitions are triggered by event-driven AI analysis, ensuring immediate action.
| Automated_Containment | Confidence score > 95% triggers immediate network isolation. | Prevents lateral movement of attackers within seconds. |