How To Create Cybersecurity Architecture Blueprint
Zero Trust, Dark web, IoT, and Anti-Spoofing principles
Are your architects instantly addressing 70% of all security questions? It can be.
Use Dragon1 to build an ISMS following ISO 27001. Protect your clouds and prevent supply chain attacks and block malicious emails with security rules and artificial intelligence.
This tutorial introduces how you can make use of Dragon1 to create Cybersecurity Architecture Blueprints.
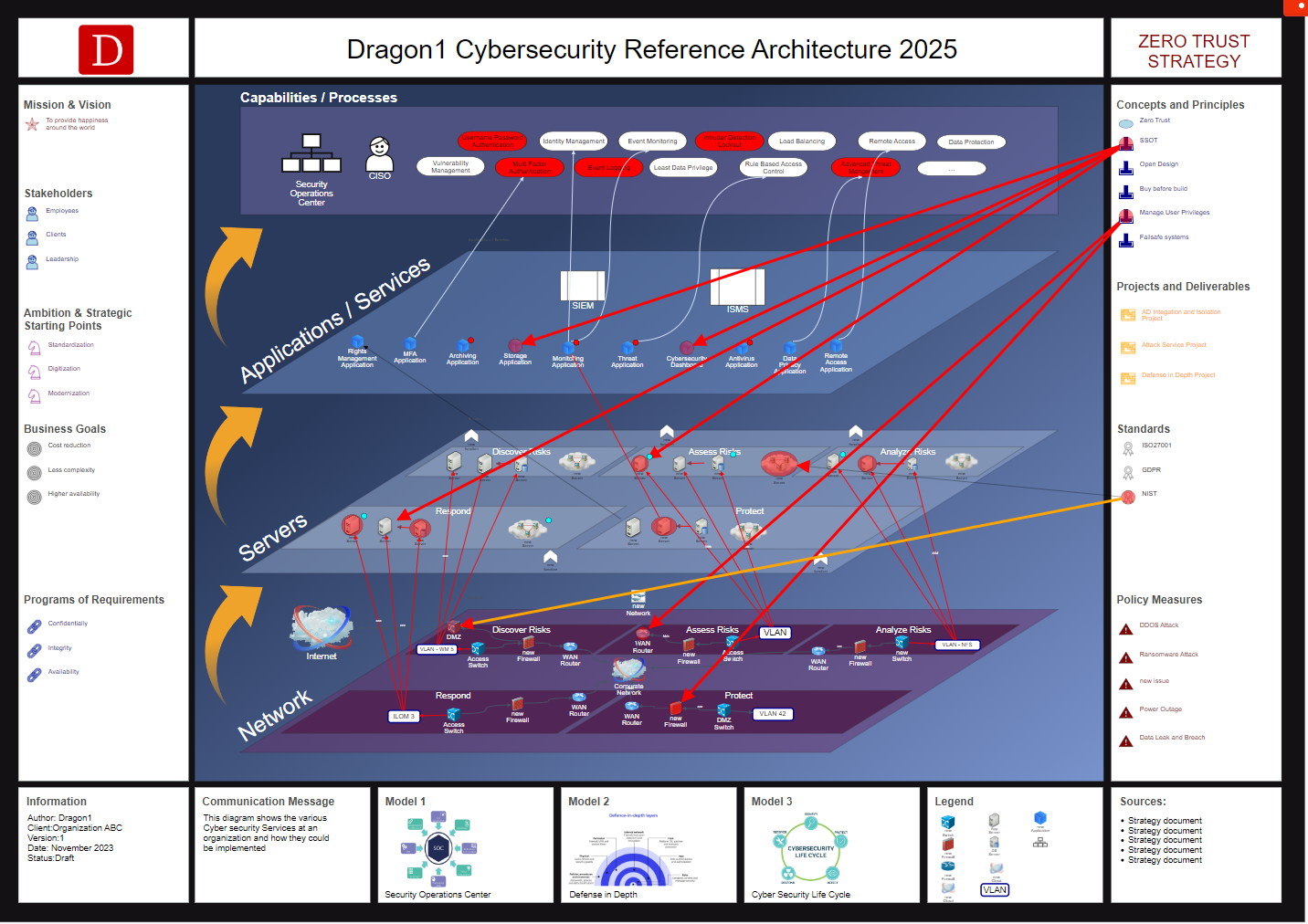
Cybersecurity views in the Cybersecurity Architecture Blueprint Atlas.
What is a Cybersecurity Architecture Blueprint?
According to the Dragon1 open EA method, cybersecurity architecture is the coherent set of security concepts (or security capabilities) of your organization.
Depending on your strategy and business model, you need certain security concepts to be implemented at a certain maturity level.
A cybersecurity architecture blueprint describes and visualizes how an organization's security controls (= security countermeasures) are positioned and how they relate to the overall systems architecture.
These security controls serve the purpose of maintaining the system's quality attributes, such as confidentiality, integrity, and availability (CIA).
Security architecture is a conceptual security blueprint of the organization, as the bridge between the strategy and transformation of the organization.
Today, security plays a vital role in the Enterprise Governance of an organization. Dragon1 helps to get enterprise security architecture linked to the governance processes, IT policies, and IT auditing, and supports CxOs in selecting appropriate measures.
Read more about Security Architecture in the Resources section.
Building Common Insights to Enable Impactful Decisions
To have a group of key stakeholders gain common insights and an overview of the current security situation and be ready to make impactful decisions for the organization's benefit and future, more and more organizations visualize their enterprise security architecture with specific visualizations called management report views.
Cybersecurity Reference Architecture Blueprint.
Security Views
Create the following common security views:
- Management Overview – How well are the top 10 key strategic cybersecurity measures taken?
- Roadmap View – When are certain cybersecurity measures going to be implemented, and what part of the IT infrastructure will be impacted?
- Security Data Breach View – Where, when, why, and how did security data breaches affect our IT infrastructure (networks and components), Data, and IT System?
- GDPR View – How well do we align with the GDPR rules for private and sensitive data?
- Confidentiality View – How well do we secure, provide, and maintain the business-required confidentiality of the IT infrastructure, Data, and IT systems?
- Integrity View – How well do we secure, provide, and maintain the business-required integrity of the IT infrastructure, Data, and IT systems?
- Availability View – How well do we secure, provide, and maintain the business-required availability of the IT infrastructure, Data, and IT systems?
- Skills & Education View – What knowledge and skills do we have or do we need to gain/develop, as is required by the security architecture, to maintain a secure IT operation?
- Documentation View – Which parts of the IT infrastructure are documented as mandatory?
- Compliance View – Which IT infrastructure components, data, and systems are (not) compliant with the standards?
- Business Process View – Which (lack of) compliance on standards in the IT infrastructure has (positive/negative) impact on certain processes?
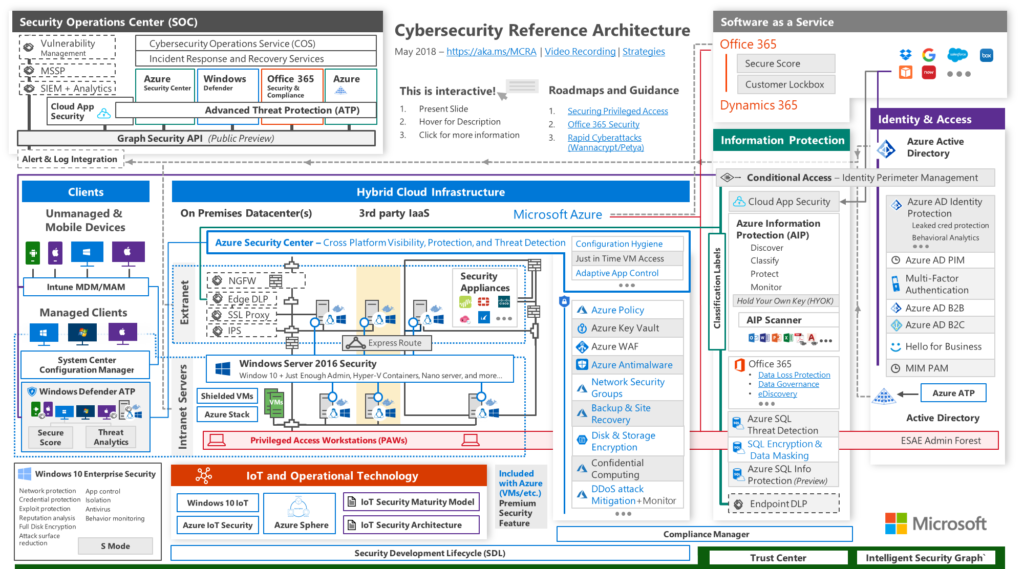
Microsoft Cyber Security Architecture Example
All cybersecurity architecture blueprints show relationships and dependencies between IT components within a context.
Create the Microsoft Cybersecurity on Dragon1 platform.
Create Cybersecurity Architecture Blueprints in 14 steps. Log in or sign up for a free trial today.